Everything You Need to Know About Passwords

Importance of a strong and secure password
Strong passwords are extremely important as they prevent unauthorized access to your digital accounts and devices.
Complicated and long passwords will make it more difficult for a hacker to crack it, whether by guessing or a brute-force attack (i.e., attackers computer automatically thousands of combinations per second and trying every possible combination of numbers, letters or special characters in an attempt to discover your password). The longer and more complex your password is, the less likely the attacker is to succeed and the more security it provides for your account.
Your accounts are where you store a great deal of sensitive information that you don’t want to have stolen or abused. The more important the account, the higher the stakes. Therefore, taking care of your account password, along with other forms of account protection, is crucial.
Your Passwords Should Never Include Any of These

- any combinations of phone numbers and addresses, or your personal and family information (including birthdays, anniversaries, pet names, middle names, relatives, friends etc).
- any string with sequential numbers or letters (most often used passwords are 123456, qwerty, password – all hacked in under a second by a bruteforce attack).
- your name in any form — first, middle, last, maiden, spelled backwards, nickname or initials.
- any ID number or user ID in any form, even spelled backwards.
- any part of your userid or username, despite possible variation.
- any common name, e.g., John, Sue, Joe. And to be fair, any name in general really.
- words in the dictionary that a hacker can easily bruteforce with the help of a dictionary program.
- any word that exactly matches a word in a dictionary, forward, reversed, or pluralized, with some or all of the letters capitalized, or with any of the following substitutions that hackers and bruteforce programs account for: a = 2 or 4, e = 3, h = 4, i = 1, l = 1, o = 0, s = $, s = 5, z = 5, etc.
- passwords of fewer than eight characters (preferably more).
- acronyms, geographical or product names, and technical terms.
- any entirely numeral passwords, e.g., your license-plate number, social-security number, TAX ID or TIN number.
- names from popular culture, e.g., Harry_Potter, Family_Guy, Eminem, Snoopy.
- a single word either preceded or followed by a digit, a punctuation mark, up arrow, or space.
- words or phrases with all the vowels or spaces deleted.
- words or phrases that do not mix letters, numbers, special characters, and upper and lower cases. Best not to use words and phrases at all.
Why Should Dictionary Words Not Be Used In a Password?

If you only use words from a dictionary or a purely numeric password, a hacker only has to try a very limited list of possibilities. A hacking program can try the full set in under one minute – the more computing power at hackers disposal, the faster the bruteforce process is. If you use the full set of characters and the techniques listed in this article, you force a hacker to continue trying every possible combination of letters, numbers and special characters to find yours. Most password crackers have the ability to try millions of variants per second, so the more algorithmically complex and random your password, the better.
Choosing a Strong and Secure Password

So, with all these limitations in place, how can you create a solid password that you can remember?
You can come up with your own system for this. For instance, you can write any sentence you like, then take the initials of each word and spice them up with a combination of numbers, lower/upper cases, and special characters.
Replacing a letter within a word with another letter, symbol or combination can be done as well, but don’t be too obvious about it, as replacing o with 0 or a with 2 or i with 1 in otherwise dictionary word passwords is something that hackers are prepared for. It is definitely better than nothing, but replacing 0 with () would be stronger as it’s not as obvious and also makes your password longer. Generally speaking, using actual words, replaced letters or not, should be avoided altogether.
Examples of Decent Passwords You Can Remember
| Phrase You Can Easily Remember | First Letters | Derived Password | Length |
|---|---|---|---|
| “I am more than just my mama’s pretty boy!” | iamtjmmpb | 1@mTjMmPb! | 10 |
| “So long and thanks for all the stinky fish” | slatfatsf | 5L@tf@t$F | 9 |
| “Best Series Ever: The Fresh Prince of Bel-Air” | bsetfpoba | B$3:Tfp0B-@ | 11 |
| “Rarely is the question asked: Is our children learning?” | ritqaiocl | R!tQa:1ocL? | 11 |
| “Fool me once, shame on… shame on you. Fool me—you can’t get fooled again” | fmososoyfmycgfa | Fm0,so…$()U.fm-Ycgf@ | 22 |
| “What Are You Doing, Step Bro!?” | waydsb | w4Ud$B!? | 8 |
Advanced Passwords (Unique, Long and Complex)

An even better solution would be to use a password generator, such as the ones offered built-in by quality password managers like BitWarden, LastPass or 1Password, and generate an entirely random, complex and long string of characters.
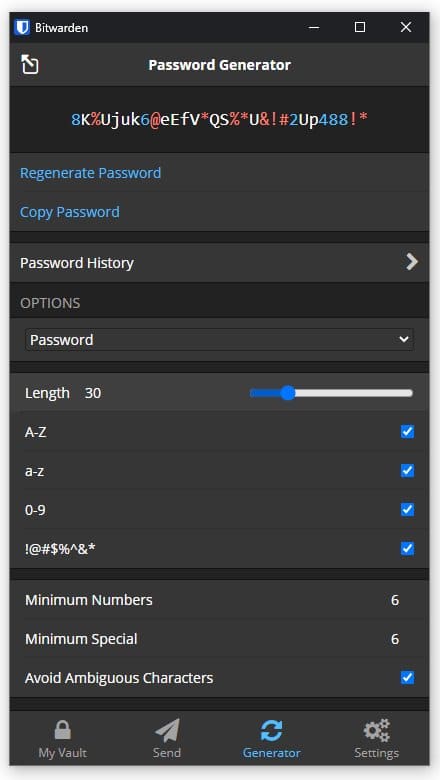
Here is an example of a high quality randomized 30 character password generated by BitWarden password manager:
8K%Ujuk6@eEfV*QS%*U&!#2Up488!*
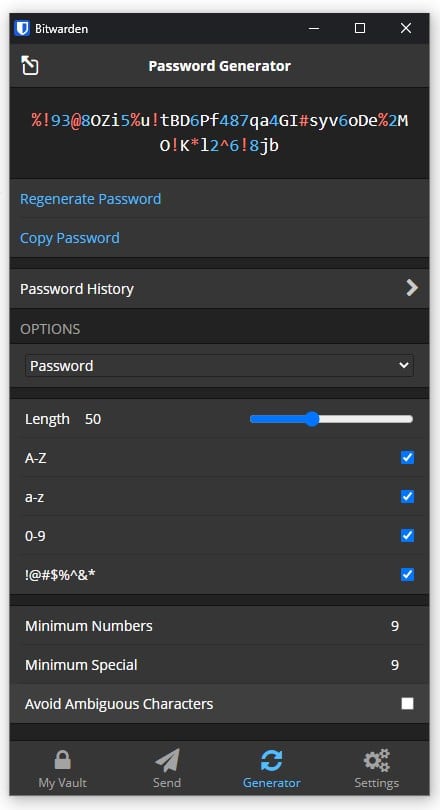
Example of a high quality randomized 50 character password (while perhaps excessive for most intents and purposes, if you are storing your passwords within a password manager anyway, then you might as well go with passwords as long as the websites will allow):
%!93@8OZi5%u!tBD6Pf487qa4GI#syv6oDe%2MO!K*l2^6!8jb
Settings used to generate the above passwords, though you can adjust the parameters to your liking, as long as you stick to the three main rules: randomness (should not make sense), complexity (mix of letters, cases, numbers and special characters) and length:
Effect of Length and Complexity on Password Security
Allowed character sets are typically numbers, upper and lowercase letters and a given set of symbols. For example:
| Character Set | Characters | Number of Characters |
|---|---|---|
| Numbers | 0123456789 | 10 |
| Lowercase Alpha Set | abcdefghijklmnopqrstuvwxyz | 26 |
| Uppercase Alpha Set | ABCDEFGHIJKLMNOPQRSTUVWXY | 26 |
| Special Characters | !”#$%&'()*+,-./:;<=>?@[\]^_`{|}~ | 32 |
If we assume that the password is only 8 characters long, the table below shows the most amount of possible combinations hacker needs to try, before cracking your password:
| Character Sets used in Password | Calculation | Possible Combinations |
|---|---|---|
| Dictionary Words (in English): (Debatable, but lets say ~600,000 words) | — | 600.000 |
| Numbers Only | 10^8 | 100.000.000 |
| Lowercase Alpha Set only | 26^8 | 208.827.064.576 |
| Full Alpha Set (Lowercase + Uppercase) | 52^8 | 53.459.728.531.456 |
| Full Alpha Set + Number Set | 62^8 | 218.340.105.584.896 |
| Full Set of allowed characters (incl. a 32 special character set) | (10+26+26+32)^8 | 6.095.689.385.410.816 |
Number of character sets used is not the only thing that the amount of possible combinations depends on.
The longer your password, the more secure. If we take the full set of allowed characters (the last line in the table above) and increase the password length, the possible combinations jump exponentially!
- 7 Characters > 64.847.759.419.264 (65 trillion) Combinations
- 8 Characters > 6.095.689.385.410.816 (6 Quadrillion) Combinations
- 9 Characters > 572.994.802.228.616.704 (573 Quadrillion) Combinations
- 10 Characters > 53.861.511.409.489.970.176 (54 Quintillion) Combinations
The more possible combinations there are, the longer it takes to crack a password.
If unsure about your password quality, Microsoft users can use the Microsoft security password checker, while Mac users can check theirs with the built-in Password Assistant.
Use a Password Manager to Remember Your Complex Passwords

“But complex passwords are not practical to type in and are as hard to remember as they are to crack…”
That is correct, and the better the password, the less likely you are to remember it. Furthermore, manually typing in 30 character passwords can be very time consuming and not practical at all. With a growing number of websites and apps that we frequent daily, remembering a complex and unique password for each and every one of them seems like an impossible task. This alone is the main reason why so many people just recycle and use the same password for many websites. While practical, easy and fast, it is also a huge security concern and should never be done. Thankfully, you do not have to choose between security and comfort, as you can use a quality password manager to store and access all your complex passwords safely, locked behind a single master password that you have to remember. You can further secure your password manager of choice using any of the available two-factor authentication (2FA) methods, though most of your important accounts should have their own 2FA solutions enabled anyway. None the less, an additional 2FA step for your password manager is desired.
If you use a password manager, it is very important to use a good master password, as the security of your password manager and all the passwords it contains depends on it. Do not choose a very short and easy to break master password as that would defeat the purpose of complex passwords it is supposed to protect, but it also does not have to be as complex as 30+ character passwords we suggest otherwise, as there is another trick one can use to further protect the passwords held within a password manager. PEPPER.
Problem: Complexity
Solution: Password managers
Always Pepper Your Important Passwords

If you don’t trust password managers or fear “putting all your eggs in one basket”, then the peppering method is for you.
“Pepper” is an additional secret code or phrase that you manually append to your otherwise auto-filled passwords and store nowhere. It can be unique for every password, which offers best security, or you can have a single pepper phrase for all, if you prefer practicality over security.
While majority of your password can be stored in the password managers database (a random and extremely complex combination of 30 characters for example), a pepper (preferably something you can remember) must be stored separately to prevent your password from being stolen by the attacker in case of a password manager database breach.
Pepper is a secret part of your password that you always type in manually, after the password manager fills out the complex majority of your lengthy password. While this adds an extra step to your log-in process, it also makes your passwords considerably more secure. It is probably not necessary for most of the low consequence websites you frequent, but you should definitely use it for the important ones, such as those having to do with finances, having access to your credit cards, ability to place orders, or post public messages in your name, etc. This way, even if your password manager is breached, the attacker is still missing a key part of your password, on top of any 2FA solution you have enabled for the accounts.
Password Peppering Example:
Website: www.youtube.com
The real password (combination of the saved password and pepper): S25u%364Sd@G@$MXm7e$*ye7$
What the password manager has saved (part that is auto-filled): S25u%364Sd@G@$MXm7e$*
Pepper (part that you add manually during the log-in): Ye7$
The pepper used in the above example was derived from first and last letter (Y, e) of the website’s domain name, the number of letters in the domain (7), and a special character of choice (in this case $, though can be anything). Obviously, this is just an example and you are best off finding your own method of coming up with easily memorable yet unique peppers. Pepper can be anything, as long as you have a method of making it easy to remember and are able to type it in fast enough, so it does not become too burdensome and time consuming, defeating the purpose of using the password manager in the first place.
Peppering your passwords is sometimes also called salting, secret salt, double-blind passwords, and password splitting, but peppering is the more correct term so that is what we use.
Problem: Password managers can potentially get compromised
Solution: Pepper your important passwords and use two factor authentication for your password manager as well for separate important websites and accounts
Principles of Good Password Security Practice
- Follow the password creation suggestions above
- Do not “recycle” your passwords and use the same password for more than one account, or use passwords that have been used in the past
- Use Two-Factor Authentication (2FA) for your important accounts whenever possible! Our preferred 2FA solution is a physical authentication key such as Yubikey, but you can also use an app for your smart phone, such as Google Authenticator, or verification over SMS etc. Anything is better than a password only.
- Don’t save passwords or use “remember me” option on public computers. Any password used on a public computer should be considered potentially compromised, making 2FA all that more important.
- Always make sure the website you are entering your passwords into is the correct one, by doublechecking the domain name. Phishing scams mimicking other websites and their domains are a very common source of breaches.
- Never provide your login credentials, especially passwords, to people claiming to be from “support” as it’s likely a scam. You may provide your username to identify yourself if you are sure about their identity, but never the password, as real support should have means to assist you without one
- Never store usernames and passwords in an unencrypted computer file or easily accessible paper
- Update your important account passwords regularly (at least every 6 months), especially if they offer no 2FA protection
- Always “pepper” your important passwords, especially if using password managers to store your credentials. Never store your pepper within the password manager as that would defeat its purpose.
- If you must share a password with a third person, you may use a site like OneTimeSecret. This site creates a link to a page with your password info (or whatever info you choose), and once the page is viewed once, it is gone forever.
- Use proper antivirus protection for your computer and run regular virus scans
- Should be needless to say, but never disclose usernames and passwords to third parties